In general, when we search any information, we usually use google. Maybe others using bing, yahoo or any search engine. But when we search for hacking, we will search with different method. But sometimes when you search for an information, can you ensure that the website or a file that you need to download is safe?
To prevent you from anything that can harm your computer, you need to know is it safe or no. Using
virustotal.com,
metadefender.com and
malwaredomainlist.com, you can know is any site you visit or any file you download is save or no.
This is what virustotal.com looks like. Usually virustotal used for checking if any website is safe or no, check if any file you download is safe or no with max upload 128 MB and check the ip address information.
For example, i search "spesifikasi hp xiaomi mi4, kelebihan dan kekurangannya" and copy that link to virustotal.
virustotal then will analyze the link that i give and give the result like this.
The result shows that the link is safe from any virus. If you can see, below the information there is list of URL scanner and the result.
Also there is additional information like website category, IP address resolution, HTTP response code and so on.
This is what metadefender.com looks like. Metadefender has similar function like virustotal, but metadefender has "LOOK UP A HASH" which is use for detecting is the has if the hash has been compromised and "SCAN AN IP ADDRESS" which check if the ip address is already compromised or no. For metadefender i will focus at the hash.
For example i put d131dd02c5e6eec4 693d9a0698aff95c 2fcab58712467eab 4004583eb8fb7f89 (MD5) and check is it compromised or no.
The result shows that the MD5 is not compromised, means that hash is safe.
You can try using SHA1 or SHA256, but i only use MD5 for this example.
This is what malwaredomainlist.com looks like. Malwaredomainlist used for checking any ip address, is it dangerous or no. Also if you want to check is website you want to visit is dangerous or no, you can search through it and if it showing the website you enter it means the website is dangerous to visit.
You can see the list of domain that is dangerous. Also you can try to search any domain that you think it's dangerous.
I try to use a save link because i kinda afraid to use dangerous link
And this is the result if the link is safe. And again, i kinda afraid to use dangerous link.
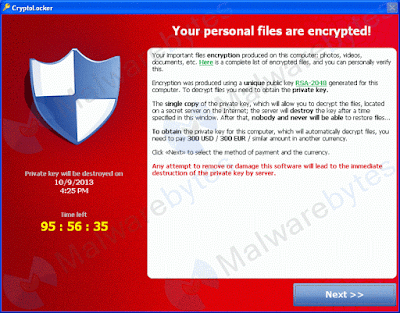
Sometimes you might want to visit any website or government website and suddenly you get something like this.
hacked website
It means that the website you visit have been hacked by someone and we can see that the website is hacked by wlingigetar.
If you want to know what website is hacked, you can use google to do "Google Hacking". "Google hacking is the use of a search engine, such as Google, to locate a security vulnerability on the Internet." (searchsecurity.techtarget.com).
When you try to do Google Hacking, for example using site:.go.id "hacked by", it will show some website that using .go.id that hacked by hacker.
some hacked website list
To sum up, everything that you think is save is not 100% save and always check if you have a doubt about the website you want to visit.
Reference link: