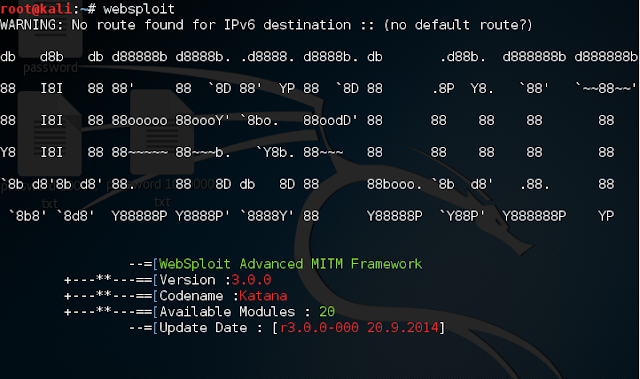
Websploit
From the display, it is similar like metasploit. Let's take a look for the modules.
Websploit modules
As you can see, websploit divides into 4 modules and it is very few compare to metasploit. For now, i only use network/mitm (Man In The Middle attack). Basically to describe Man-In-The-Middle attack, it is like the source communicate with the target, but the third person comes and eavesdropping the conversation without knowing there is a third person for the source and the target (knowing as "Intercept").
Let's back to the topic, so i choose network/mitm and to know what to do next, enter "show options".
network/mitm
Before i continue, i choose my win 2000 as the target machine and the ip address is 192.168.59.129.
win 2000
Using "show options", you can see the interface, router, target, sniffer and ssl. There are 4 types sniffer but this time i choose urlsnarf.
To start the tools, enter "run".
Back to my win 2000, now i open my Opera and i go to 9gag.com.
9gag.com in Opera using win 2000
Now back to my Kali Linux and see what is change.
We can see now there is some change in here. From that data, we can know that the target is using Opera 9.80 Presto 2.6.30 version 10.63, open 9gag website and using OS windows. Let's try another website and this time i use detik.com.
detik.com
Then go back again and see what happen.
So this time there are so many information and because of that i only capture 2 pictures. Because we are using same OS, most of the previous information is same except the site, which is detik.com.
Now let's do other thing using network/webkiller.
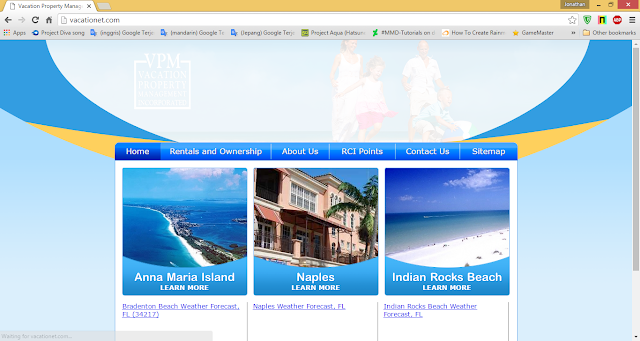
For the target, i use vacationet.com.
vacationet.com
As usual, show options and change the target.
Last, we start to attack.
When i try to visit the web again, nothings happen. I assume because i don't have enough computer to attack the target.
target still alive
So that's some websploit modules and remember to use it wisely.
Reference:
http://tools.kali.org/web-applications/websploit